Ninja Tools Access Control Counter
This shutter is designed to be utilized in those applications that incorporate counter tops or openings that require the shutter to rest on a sill.

Ninja tools access control counter. Whenever I try to view anything on this site for some time now (months), it begins to load, but then quickly flips to some blacked-out "Ninja Tools Access Control Counter" screen. It seems Access believes the form does not contain a control named txtInput_PM_EN_DRAF T. I am using Firefox and "no Script" plugin ,might this be the reason ?.
Access Control, Accessories, Wall Terminal 00 -it™, Architectural. Use a ControlCollection method that has the name Add<control class> (where control class is the class name of the content control that you want to add, such as AddRichTextContentControl), and that has a single parameter for the name of the new control. I suggest you the examine names of the controls which Access thinks the form contains.
Have questions or feedback about Office VBA or this documentation?. Show access-list displays the access control lists (ACLs) that were generated from the access control rules. Every feature is designed with simplicity in mind.
NINJA-TOOLS ACCESS CONTROL COUNTER Offline. Domain The set of records. To a page about Ninja-Tools Access Control Counter.
The Table View is not configurable, hence just proceed to Save your workflow. The same thing happens when I "Temporarily allow all this page" in NoScript options, or when I try to view the site on IE. You can enumerate individual controls, count them, and set their properties in the Controls.
To complete a missions successfully often required many tools, and these were the tools of the trade for the successful ninja warrior. =Count(*) is the way to do it, but for the record there are a couple of things wrong with you expression:. Controls.Count property (Access) 03/06/19;.
Thanh "ninja" Vinh Bui (born September 9, 1987) is a retired German professional Counter-Strike:. In this article we are going to show you how to display totals taken from your subform, and display these in controls in your main form. Berkeley Electronic Press Selected Works.
Hello Mates, Am getting a very rare type problem while I implement the aCL on 3850 switch I do get hit matches when I put a log keyword in the ACL 102 SW#sh ip access-lists Extended IP access list 102 5 permit tcp 192.168.0.0.0 0.0.255.255. The syntax for the DCount function in MS Access is:. The function then loops through each control using the Count property which contains the number of controls on the form.
When Event Count equals one, I want to override the default appearance to remove the underline and. Leave this field empty if you're human:. With the form in Design view, insert a text box control.
We are constently adding new features to deliver the right information at the right time. Here's the download link. 2 minutes to read;.
問答無用でninja-tools access control counterに飛ばされます。 戻れません。 NoScriptで、そのblogだけジャバスクリプト解禁しようにも飛ばされた先では意味がありません。. The following code example uses the AddRichTextContentControl method to add a new. Woodwork, installation, repairs, and more.
So, anyone had the same experience ?. The medium access control (MAC) protocol is primarily responsible for regulating access to the shared medium!. For each control, the Debug.Print method is used to display the Control's name.
It was a typical summer sleepover. The first section focuses on the DLookup function and it's arguments Expr, Domain and Criteria.This information roughly also applies to aggregate (totals) functions such as DSum and DCount which are. I'm using Access 10.
We can use the DCount function in Visual Basic and macro. Rolling Counter Shutters Model 500. My services might be varied, but they all come with the same promise of quality, dedication, and durability.
Visit the most interesting Hobbysupply Blog Shinobi pages, well-liked by users from Japan, or check the rest of hobbysupply.blog.shinobi.jp data below. Use DCount() Function in MS Access DCount function is a built-in function to get the number of records from the set of records or data from table, query, SQL, or Recordset. To enable support for role-based access control on a single machine, follow these steps:.
Access Object Model Reference;. Think of its a shorthand reference to the current form. Step 6 The Table View is not configurable, hence just proceed to Save your workflow.
- Pinterest で minnorukajima さんのボード「あ」を見てみましょう。。「乃木坂 齋藤飛鳥, あしゅ, 斎藤飛鳥」のアイデアをもっと見てみましょう。. In this tutorial you will learn what RFID is, how it works and how to make an Arduino based RFID door Access Control with counter and you also see who last a. Add a second page with the Add Table View option.
Open Windows Admin Center and connect to the machine you wish to configure with role-based access control using an account with local administrator privileges on the target machine. Displaying Subform Totals in a Main Form in Microsoft Access:. Dukascopy NinjaTrader Addon is a trading plugin which adds Dukascopy forex broker support to NinjaTrader.
For example, you could display the number of orders in the Orders table in a calculated control on a form based on the Products table. The cornerstone of any Microsoft Access application is the form. We need to be able to reference the subform control from the main Microsoft Access form.
The following example uses the Count property to control a loop that prints information about all open forms and. アクセス解析のninja toolsが邪魔してサイトが 「NINJA-TOOLS ACCESS CONTROL COUNTER このホームページはJavaScriptを使っています。 ブラウザの設定でJavaScriptを有効に設定してからアクセスしてください。」 と出て閲覧できない。. Expression A variable that represents a Controls object.
I have a control named Event Count in a summary datasheet form.If the value of Event Count is greater than one, I'll use an onClick event to link to a pop-up form containing the individual event details.By default, the control is formatted to appear as a hyperlink. This can be a table or a. Use the DCount function when you must count records in a domain from within a code module or macro, or in a calculated control.
Hobbysupply.blog.shinobi.jp is a web project, safe and generally suitable for all ages. The same thing happens when I "Temporarily allow all this page" in NoScript options, or when I try to view the site on IE. For those of you wanted the gun mod for Skyrim as featured in Skyrim Mods 85.
Control Policy, Access Control Rule and by Count, Initiator IP and Responder IP fields. On the Overview tool, click Settings > Role-based access control. Data retrieval functions, DLookup, DCount, DSum and more.
Enter the expression in the form =Count (primarykey) as the control's Control Source property. It refers to the current instance of the class in which the code is running. Find Ninja kitchen tools at Lowe's today.
Please see Office VBA support and feedback for guidance about the ways you can receive support and provide feedback. It can be a string expression. Operands in expr can include the name of a table field or function (which can be either intrinsic or user-defined but not other SQL.
SERVICES Life Long Craftsman. You can use the DCount function to count the number of records containing a particular field that isn't in the record source on which your form or report is based. The log-input option enables logging of the ingress interface and source MAC address in addition to the packet's source and destination IP addresses and ports.
2 minutes to read;. The Count () function takes just one. 3 nodes of ISE in PAN failover running version 2.2 and an external web server.
To pass through locked doors, the ninja would arm themselves with lock picks. Wayne Dalton’s Model 500 Rolling Counter Shutters provide the perfect solution for smaller openings that require visually appealing access control. DCount ( expression, domain, criteria ) Parameters or Arguments expression The field that you use to count the number of records.
Controls object (Access) 03/06/19;. Your access control system is only as good as the accessories you have to support it -- and we’ve got that covered!. Allready tried to quickly allow the modtype.doorblog site.
Learn how to change a display control to a check box in Access. Learn how to change a display control to a check box in Access. Whenever I try to view anything on this site for some time now (months)' date=' it begins to load, but then quickly flips to some blacked-out "Ninja Tools Access Control Counter" screen.
Geographical access control may be enforced by personnel (e.g., border guard, bouncer, ticket checker), or with a device such as a turnstile.There may be fences to avoid circumventing this access control. Global Offensive and Counter-Strike player of Vietnamese descent. In this op-ed, Rose Schnabel celebrates Thanks Birth Control Day by calling for over the counter birth control access for young people.
The Microsoft Access DCount function returns the number of records from an Access table (or domain). Sync was born from a desire to make your life easier. Add a new page for a workflow with the Add Page option, define its name and sort the column fields by Access Control Policy, Access Control Rule and by Count, Initiator IP and Responder IP fields.
Step 5 Add a second page with the Add Table View option. The Me keyword can only be used in VBA code, not in an expression in a control's properties sheet. Calculates the number of records returned by a query.
DCount Syntax DCount(Expression, Domain, Criteria optional) Expression identifies the field that you want to count records. An alternative of access control in the strict sense (physically controlling access itself) is a system of checking authorized presence, see e.g. You can use the Count property to determine the number of items in a specified collection.
Thou not sure if it was set. The ACLs provide an initial filter and attempt to provide quick decisions whenever possible, so that connections that should be dropped do not need to be inspected (and thus consume resources unnecessarily). Count(expr)The expr placeholder represents a string expression identifying the field that contains the data you want to count or an expression that performs a calculation using the data in the field.
The log and log-input Access Control Entry Options The log and log-input options apply to an individual ACE and cause packets that match the ACE to be logged. To add a content control at the current selection. Microsoft Access VBA Referring to Forms and Controls by FMS Development Team.
An RFID system consists of two main components, a transponder or a tag which is located on the object that we want to be identified, and a transceiver or a reader The RFID reader consist of a radio frequency module, a control unit and an antenna coil which generates high frequency electromagnetic field. In what was her final dissent, the late Justice Ruth Bader Ginsburg fiercely advocated for workers to have their birth control covered by insurance regardless of their employers’ beliefs.In the decision, the Supreme Court ruled 7-2 in the midst of the COVID-19 pandemic to uphold the Trump administration’s rules that allow companies to deny insurance coverage of birth control to employees. My friend and I were.
The Controls collection is a member of the Form, Report, and SubForm objects. This value in a back-off counter!. Not only this specific link, but all to this site.
Hi, we are deploying a new PoC enviroment and we are running in a strange problem. For every time slot that passes without activity on the network, the counter is decremented and the device can attempt transmission when. It seems that counter for the active endpoints is not incrementing.
I suggest you the examine names of the controls which Access thinks the form contains. Professional Deribit Binance Bitfinex Bitcoin Ninjatrader 8 Addons. You can use the Data retrieval functions such as DLookUp in an expression or in a VBA function to return a field value in a table.
The plugin supports historical tick/minutes data backfill, real time data streaming, and order handling with server side OCO support.
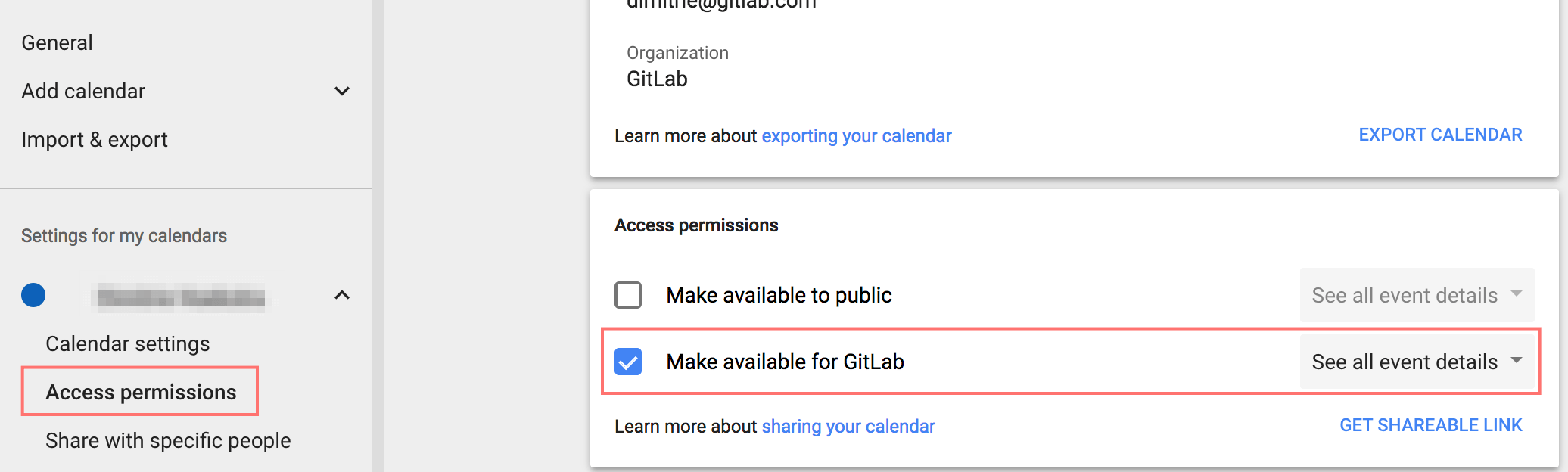
Tools And Tips Gitlab

Amazon Com Ninja Professional Countertop Blender With 1100 Watt Base 72 Oz Total Crushing Pitcher And 2 16 Oz Cups For Frozen Drinks And Smoothies Bl660 Gray Electric Countertop Blenders Kitchen Dining
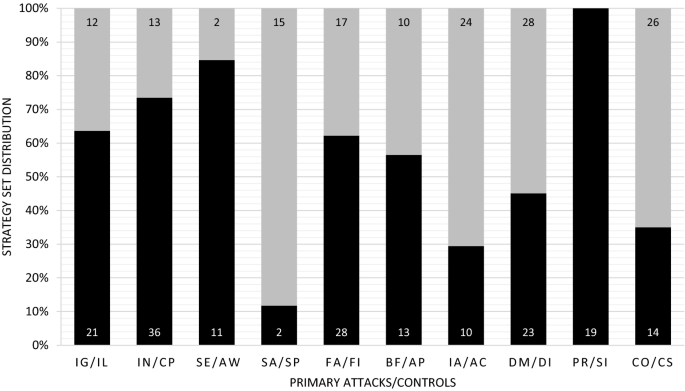
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink
Ninja Tools Access Control Counter のギャラリー

Ninja Professional Plus Kitchen System With Auto Iq Black Stainless Steel Bn801 Best Buy

The Crm Ninja Thoughts Musings From A Dynamics 365 Ninja
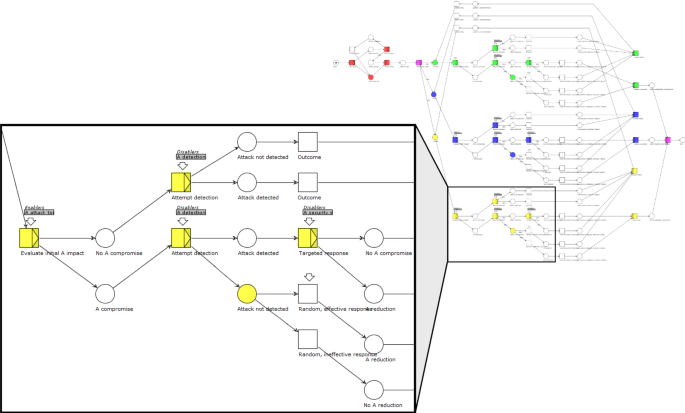
J1enk6sgyarf9m

Ninja Doing It Right Ffxiclopedia Fandom

Ninja Tools Access Control Counter 久保 久保史緒里
Q Tbn 3aand9gcs Mfgasz3v7 Lfrit29phlycpaf0rblozuzosomne Usqp Cau

Ninja Tools Access Control Counter 美容 美髪 オルチャンガール
Versprite S Analysis Of A Vulnerable Window Named Pipe Application

Amazon Com How To Be A Productivity Ninja 19 Updated Edition Worry Less Achieve More And Love What You Do Ebook Allcott Graham Kindle Store

The Crm Ninja Thoughts Musings From A Dynamics 365 Ninja

The Things That Are Better Left Unspoken A Blog By Sander Berkouwer

Ninja Tools Access Control Counter 齋藤飛鳥 あしゅ 美しい人

Ninja Stainless Steel Foodi Digital Air Fry Oven Convection Oven Toaster Air Fryer Flip Away For Storage Sp101 The Home Depot

Refreshblocker Ninja Tools Access Control Counter をカウンター Naver まとめ
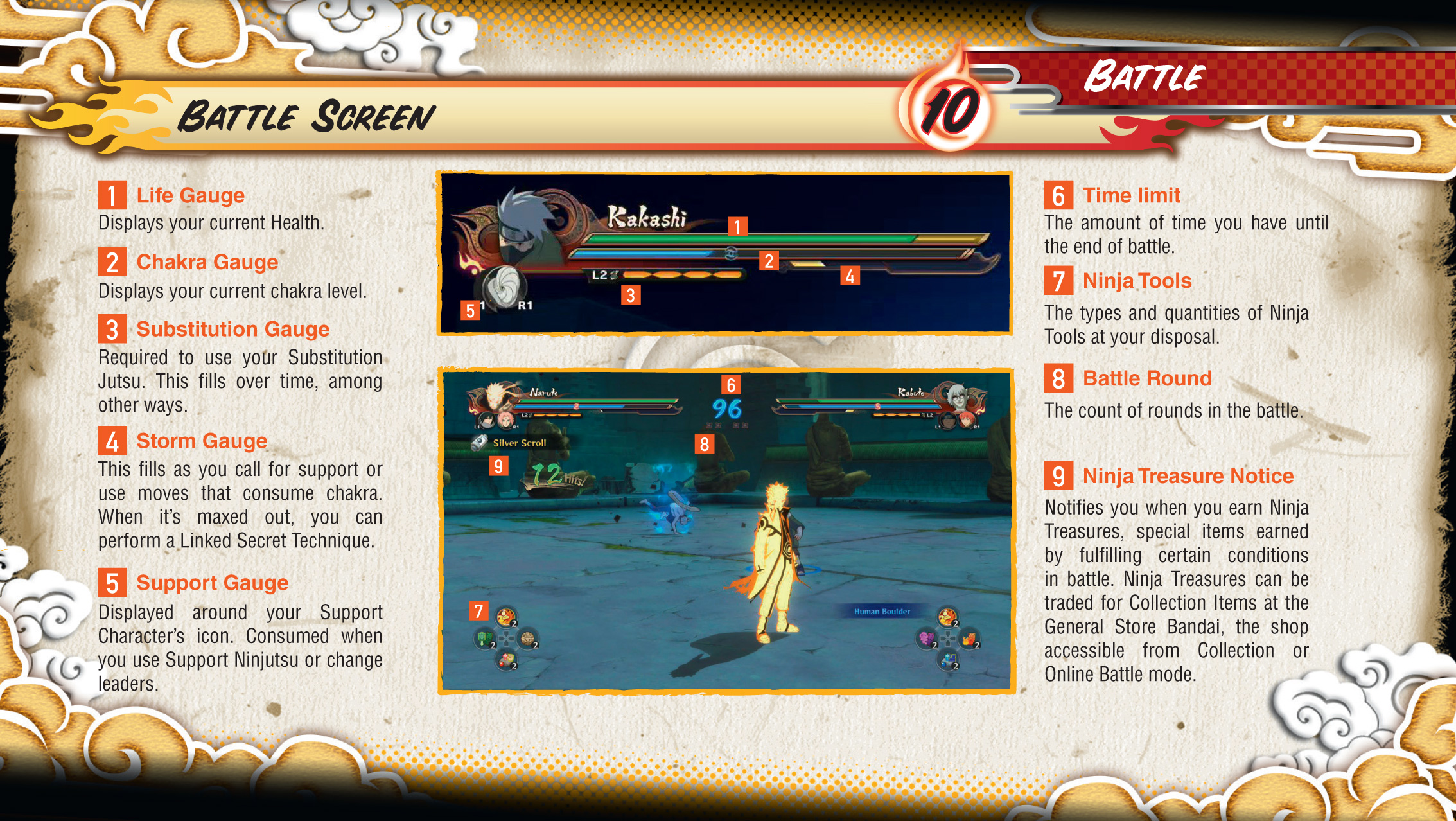
Naruto Shippuden Ultimate Ninja Storm 4 Playstation 4 Online Manual

How To Use The Ninja Foodi Volume Two Pressure Cooking 101 The Salted Pepper

Wireshark User S Guide
Q Tbn 3aand9gctvtdfpfcimnqwqbbrxps9i8okx09vgyxn0oz3ldidknykujotq Usqp Cau

Wireshark User S Guide
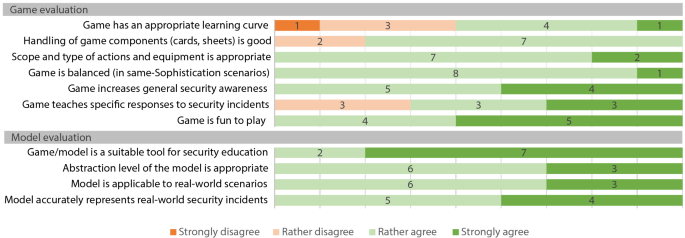
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

Ninja Stainless Steel Foodi Digital Air Fry Oven Convection Oven Toaster Air Fryer Flip Away For Storage Sp101 The Home Depot

The Crm Ninja Thoughts Musings From A Dynamics 365 Ninja
Top 51 Log Management Tools For Monitoring Analytics And More

Babymetal Darake Com At Wi Ninja Tools Access Control Counter

Ninja Tools Access Control Counter 齋藤飛鳥 乃木坂 齋藤飛鳥

Ninja Tools Access Control Counter 与田

The Crm Ninja Thoughts Musings From A Dynamics 365 Ninja
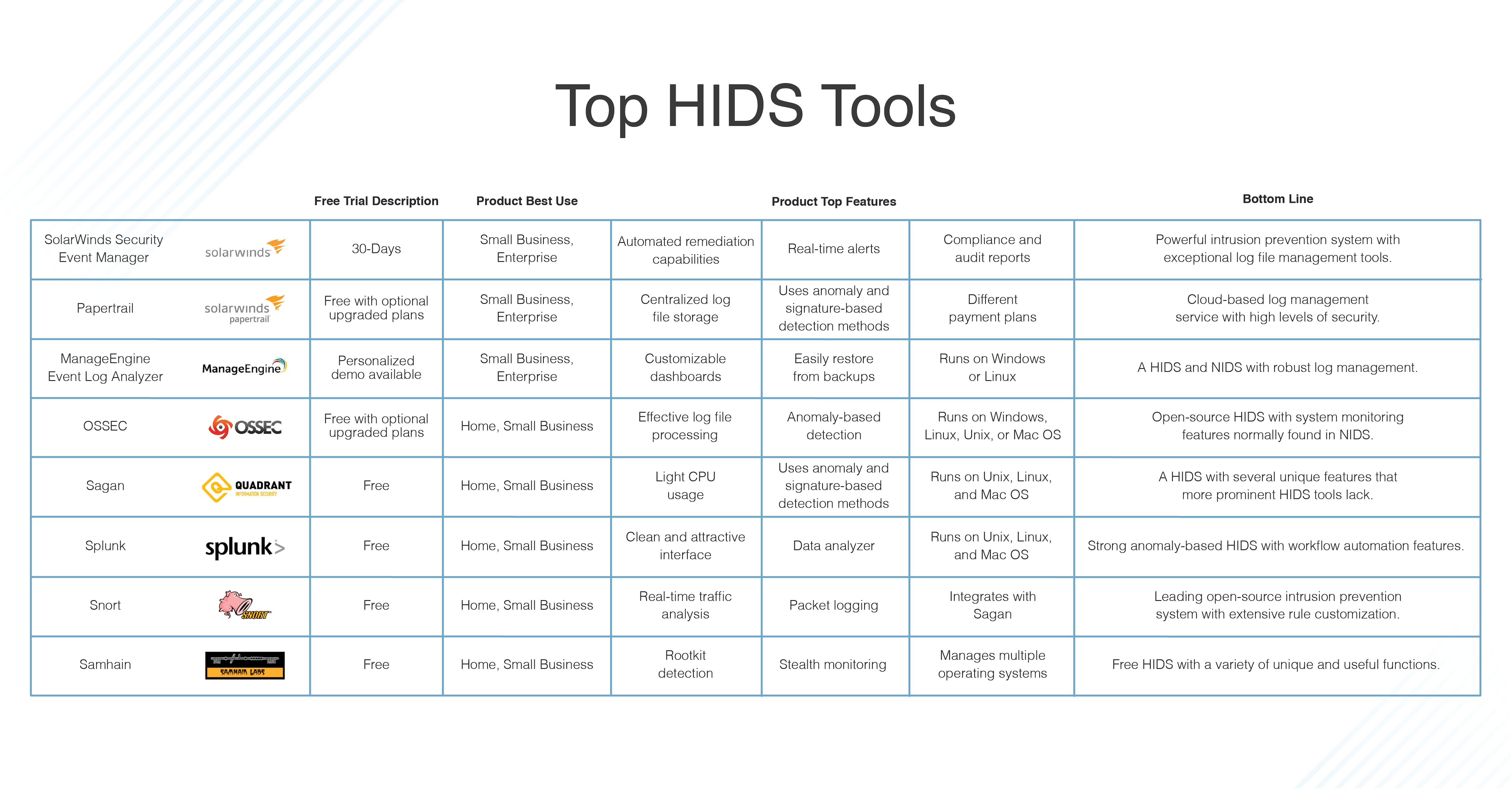
8 Best Hids Tools Host Based Intrusion Detection System Dnsstuff
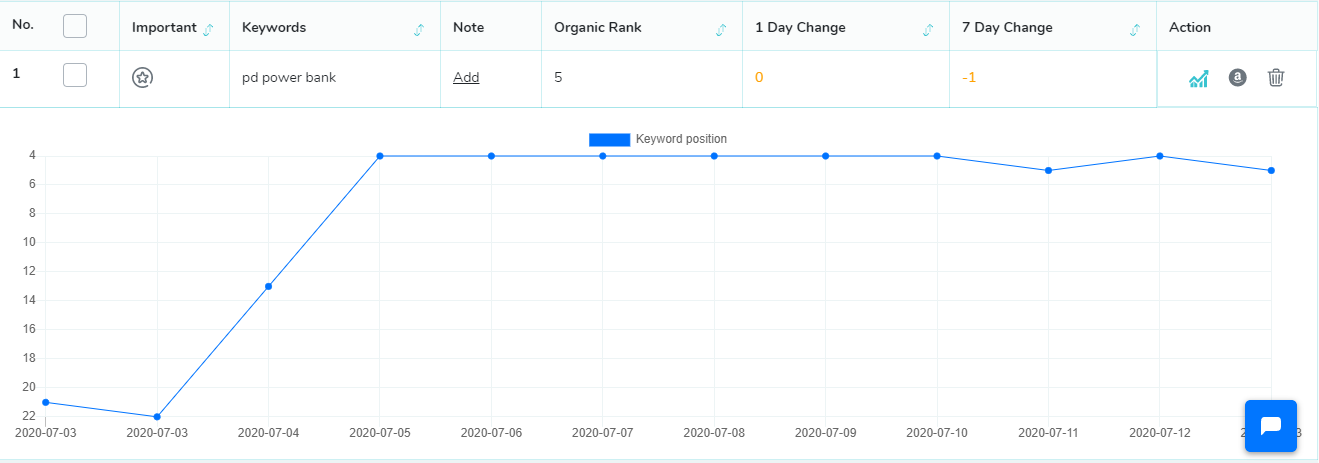
58 Top Amazon Seller Tools Of Best Fba Softwares Complete List

Amazon Com Ninja Kitchen System 10 Black 0 Electric Countertop Blenders Kitchen Dining

Amazon Com Ninja Ce251 Programmable Brewer With 12 Cup Glass Carafe Black And Stainless Steel Finish Kitchen Dining

The Crm Ninja Thoughts Musings From A Dynamics 365 Ninja

Best Air Fryer Of Dash Ninja Philips Cosori And More Cnet
Versprite S Analysis Of A Vulnerable Window Named Pipe Application
2

Wireshark User S Guide
The Ninja Foodi Digital Air Fry Oven With Convection Bed Bath Beyond

58 Top Amazon Seller Tools Of Best Fba Softwares Complete List
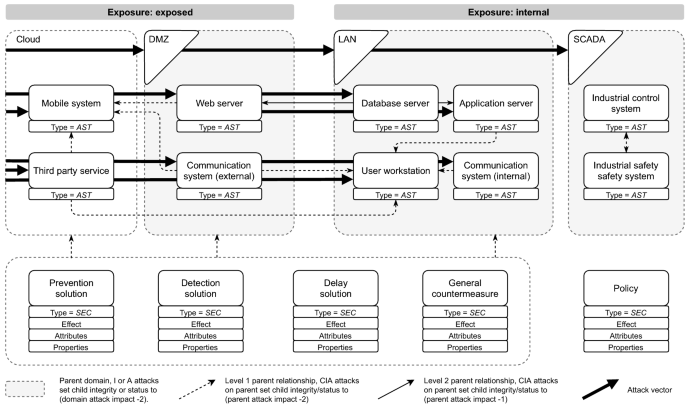
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

The Things That Are Better Left Unspoken A Blog By Sander Berkouwer

乃木坂46 Nogizaka46 齋藤飛鳥 齋藤飛鳥 乃木坂
Versprite S Analysis Of A Vulnerable Window Named Pipe Application

The Future Is Now Our New Client Area And Site Tools Are Going Live Siteground Blog
1
忍者バリアーなんて死ねばいいのに Amagrammar Programmer

Amazon Com Ninja Foodi Digital Fry Convection Oven Toaster Air Fryer Flip Away For Storage With Xl Capacity And A Stainless Steel Finish Kitchen Dining

Naruto Slugfest Guide Tips Cheats Strategies To Increase Cp Mrguider

The Crm Ninja Thoughts Musings From A Dynamics 365 Ninja

The Crm Ninja Thoughts Musings From A Dynamics 365 Ninja

Ninja Tools Access Control Counter 紅白 齋藤飛鳥 アイドル 写真

Ninja Tune Wikipedia
Versprite S Analysis Of A Vulnerable Window Named Pipe Application

Naruto Shippuden Ultimate Ninja Storm 3 Narutopedia Fandom
Visual Studio 19 Version 16 7 Release Notes Microsoft Docs

Ninja Tools Access Control Counter 紅白 乃木坂 山下美月

Amazon Com Shogun Kawasaki Ninja 400 Z400 Z 400 18 19 No Cut Black Frame Sliders Fits Abs Non Abs Models 750 4159 Made In The Usa Home Kitchen

Naruto Shippuden Ultimate Ninja Storm 4 Beginner Tips And Tricks Naruto Shippuden Ultimate Ninja Storm 4
Visual Studio 19 Version 16 7 Release Notes Microsoft Docs
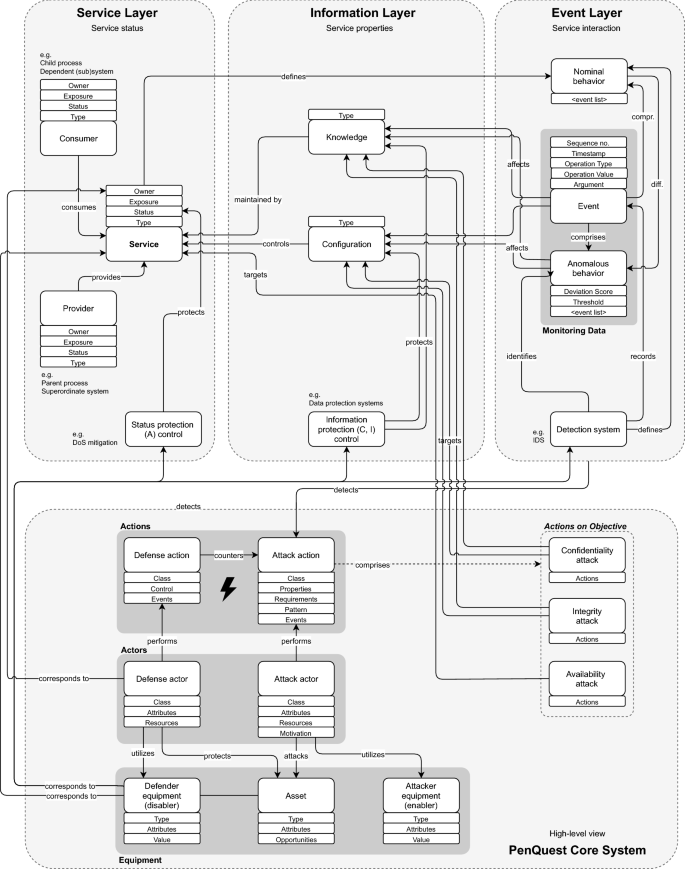
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink
The Future Is Now Our New Client Area And Site Tools Are Going Live Siteground Blog
Naruto Shippuden Ultimate Ninja Storm 4 Beginner Tips And Tricks Naruto Shippuden Ultimate Ninja Storm 4
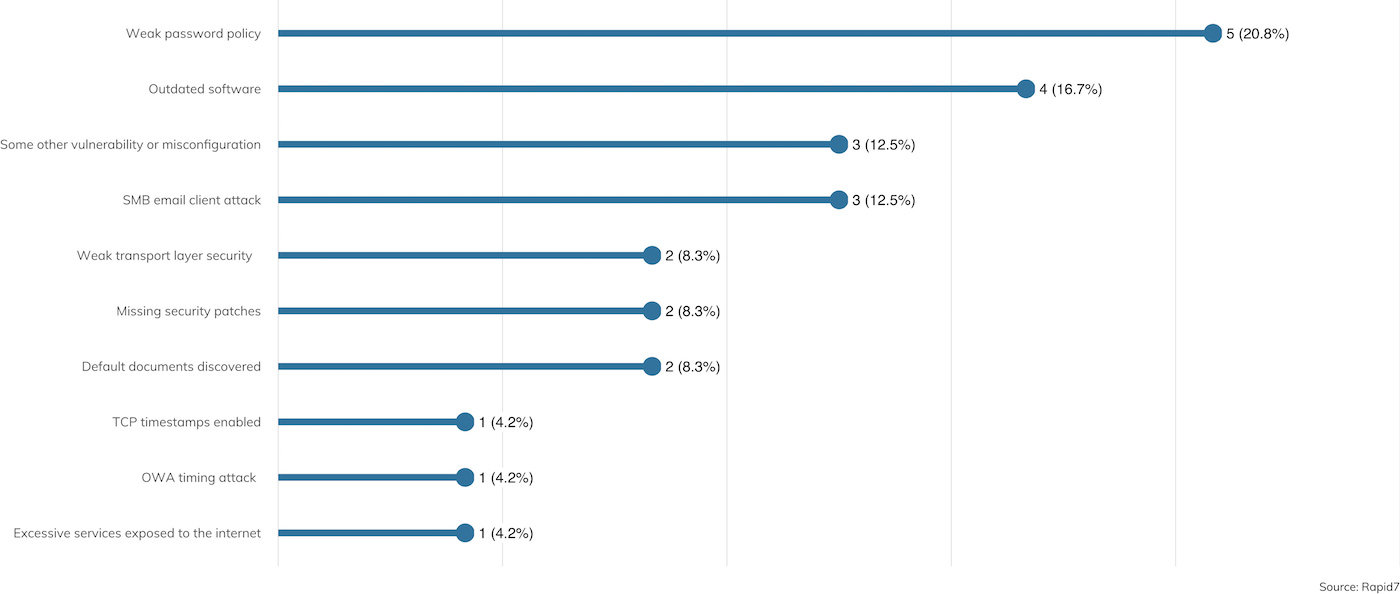
Under The Hoodie 19 Security Lessons Learned From 180 Pen Tests
Windows Virtual Desktop Technical Arm Based Model Generally Available Deployment Walkthrough It Covers All You Need To Know And Beyond Christiaanbrinkhoff Com Sharing Cloud And Virtualization Knowledge

How To Use The Ninja Foodi Volume Two Pressure Cooking 101 The Salted Pepper

Naruto Shippuden Ultimate Ninja Storm 4 Beginner Tips And Tricks Naruto Shippuden Ultimate Ninja Storm 4

Amazon Com Modern Ninja Warfare Ninja Tactics For The Modern Warrior Ebook Cummins Antony Kane Jayson Kindle Store

Q Tbn 3aand9gcq6a5oth6rjb7pqkvmjr8ncba9 Xuoty Dhma Usqp Cau

The Crm Ninja Thoughts Musings From A Dynamics 365 Ninja

Access Tobimori Ni Moe Com Ninja Tools Inc 忍者ツールズ株式会社
Ninja Stainless Steel Foodi Digital Air Fry Oven Convection Oven Toaster Air Fryer Flip Away For Storage Sp101 The Home Depot
Versprite S Analysis Of A Vulnerable Window Named Pipe Application
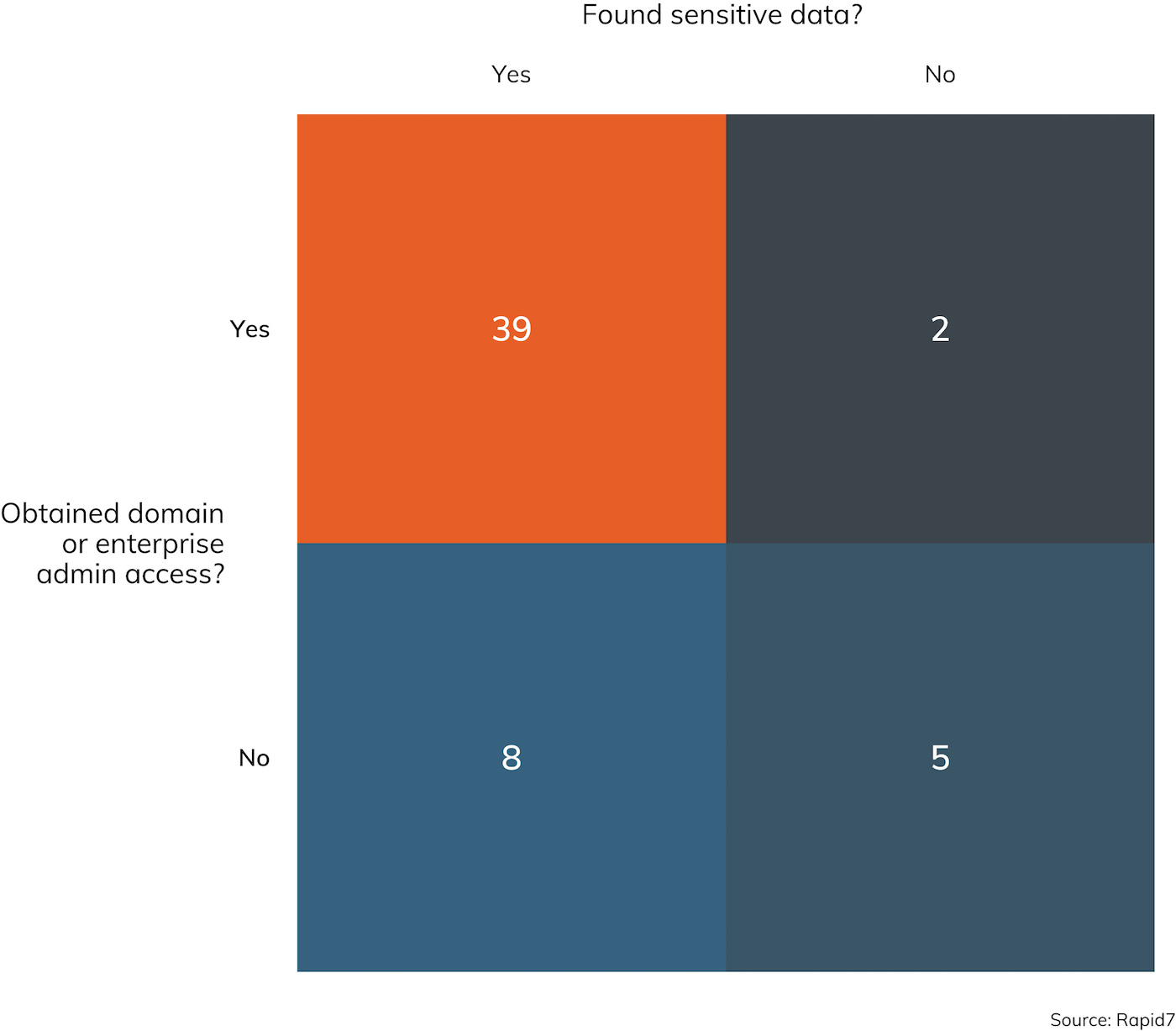
Under The Hoodie 19 Security Lessons Learned From 180 Pen Tests
Versprite S Analysis Of A Vulnerable Window Named Pipe Application

It Campus Security College And School Campus Education Security Security Today

Ninja Tools Access Control Counter
Q Tbn 3aand9gcrojtlaux Bzlb4r57mjkgcnbowfjisav74jxesntu6 Uw P48 Usqp Cau
Reverse Engineering Attacks 6 Tools Your Team Needs To Know Techbeacon
Tools And Tips Gitlab

Naruto Slugfest Guide Tips Cheats Strategies To Increase Cp Mrguider
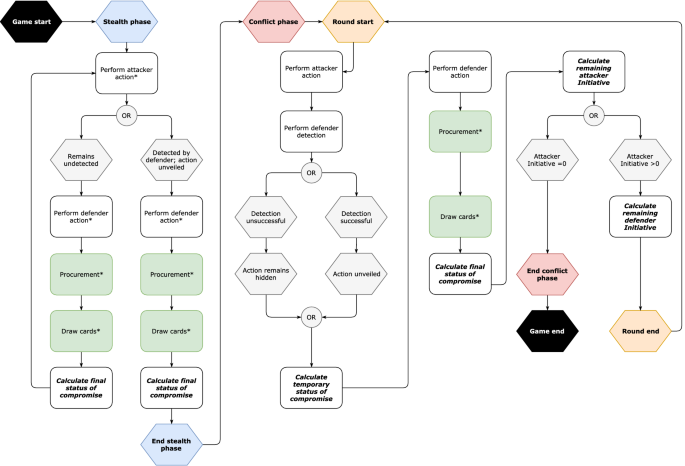
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

Ninja Tools Access Control Counter 生田絵梨花 生田 花

Nutri Ninja Ninja Blender Duo With Auto Iq Bed Bath Beyond

Amazon Com Ninja Foodi Grill Cover Black Kitchen Dining

The Crm Ninja Thoughts Musings From A Dynamics 365 Ninja

Katasuke Tōno Narutopedia Fandom

Amazon Com Ninja Auto Iq Total Boost Kitchen Nutri Blender System With 1500 Watts Professional Base Bl687co Renewed Kitchen Dining
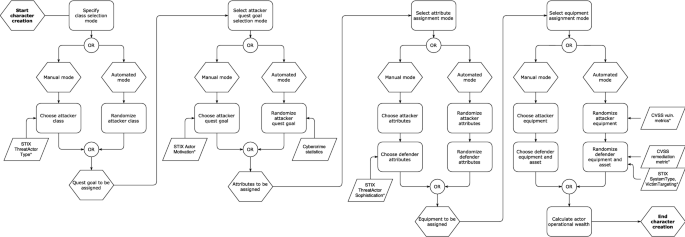
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink
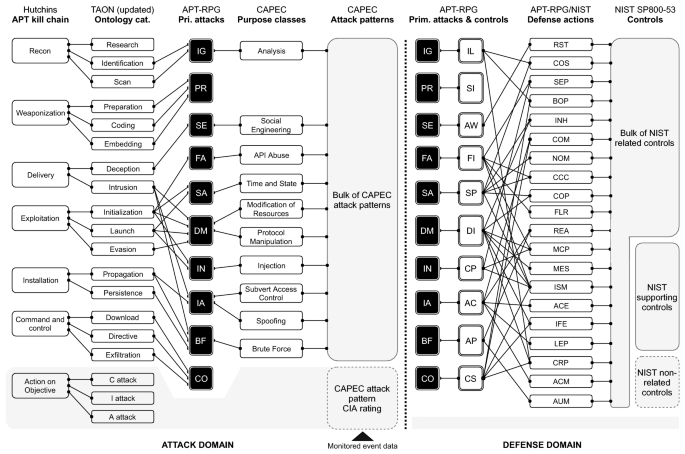
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

Wireshark User S Guide
2
Www Gigamon Com Content Dam Resource Library English Analyst Industry Report Cyber Security Annual Cyber Security Handbook And Reference Guide Vol 3 Pdf
The Best Stealth Tool Kits For Mountain Biking

The Best Stealth Tool Kits For Mountain Biking
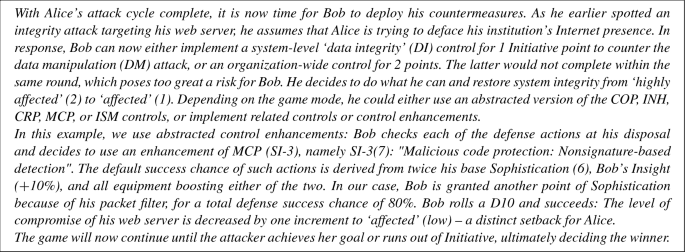
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

Wireshark User S Guide
Versprite S Analysis Of A Vulnerable Window Named Pipe Application

58 Top Amazon Seller Tools Of Best Fba Softwares Complete List

Wireshark User S Guide

Best Air Fryer Of Dash Ninja Philips Cosori And More Cnet
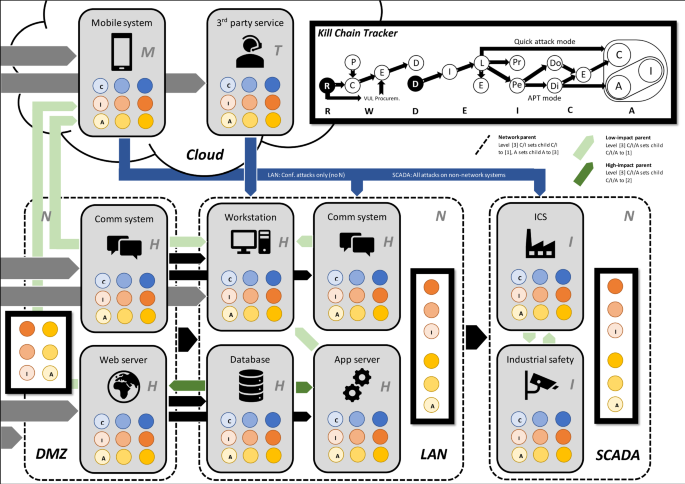
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink
2



